
How to Protect Business Data in the Cloud
How to Protect Business Data in the Cloud is a critical concern for organizations of all sizes. As businesses increasingly…

How to Protect Business Data in the Cloud is a critical concern for organizations of all sizes. As businesses increasingly…

Securing business IoT devices is a critical concern for organizations looking to leverage the benefits of connected technology while minimizing…

Protecting sensitive business documents is a critical aspect of maintaining the integrity and confidentiality of an organization. In an era…
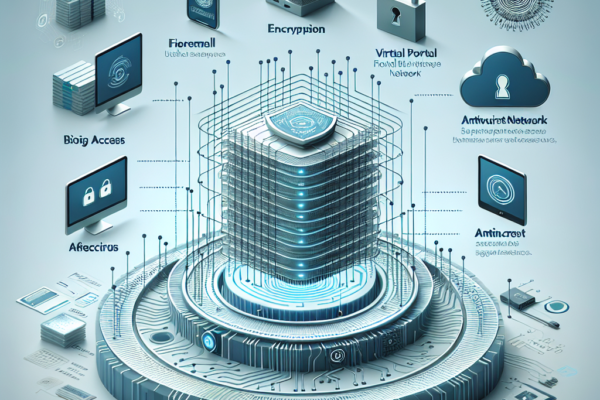
Protecting business infrastructure from cyberattacks is a critical concern for organizations of all sizes. As technology continues to evolve, so…

Securing payment processing in your business is crucial for maintaining customer trust and ensuring the longevity of your operations. As…

Identifying and mitigating security vulnerabilities is a critical aspect of maintaining a robust business security posture. In an era where…

How to respond to a cybersecurity breach in your company is a critical issue that every business must address. In…

How to Secure Business Mobile Devices is a critical topic for organizations that rely on mobile technology to enhance productivity…

Protecting your business from social engineering attacks is crucial in today’s digital landscape, where cyber threats are becoming increasingly sophisticated….

Creating strong password policies is essential for any company aiming to protect its sensitive data and maintain the integrity of…