
The Importance of Regular Security Audits
Effective security oversight is critical for organizations aiming to safeguard assets, maintain trust, and sustain growth. By adopting regular security…

Effective security oversight is critical for organizations aiming to safeguard assets, maintain trust, and sustain growth. By adopting regular security…

Continuous security monitoring has become a cornerstone for organizations aiming to protect sensitive data and maintain operational integrity across digital…

Building a robust IT strategy that prioritizes security from the ground up is essential for modern organizations seeking to protect…

Organizations are increasingly recognizing that safeguarding assets extends beyond digital firewalls. A holistic approach demands seamless collaboration between physical measures…
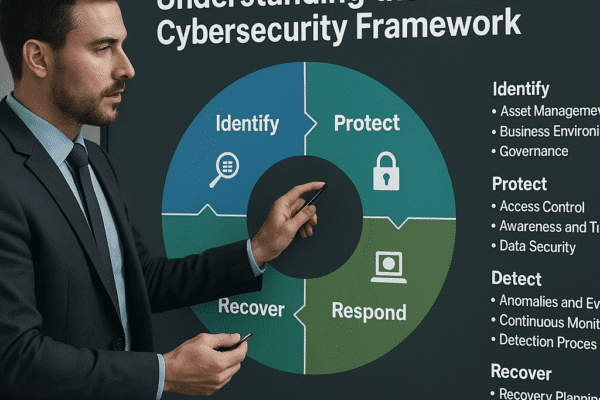
The NIST Cybersecurity Framework (CSF) has become a cornerstone for organizations seeking to strengthen their digital defenses while aligning security…

Organizations facing a breach must act swiftly to limit damage, restore operations, and protect their reputation. This guide outlines practical…
Building a comprehensive incident response framework is essential for organizations aiming to protect their digital assets and maintain operational continuity….
The role of blockchain in business security is becoming increasingly significant as organizations seek innovative solutions to protect their data…

The importance of a secure IT infrastructure in business cannot be overstated, as it serves as the backbone of modern…
The role of behavioral analytics in security monitoring has become increasingly vital as organizations strive to protect their assets and…