The NIST Cybersecurity Framework (CSF) has become a cornerstone for organizations seeking to strengthen their digital defenses while aligning security initiatives with business objectives. By delivering a structured yet flexible approach, the Framework enables enterprises of all sizes to assess current security postures, manage risks effectively, and foster a culture of continuous improvement. This article explores core components of the CSF, practical guidance on implementation within a business environment, the advantages and potential obstacles, and recommended best practices for a sustainable cybersecurity strategy.
Core Components of the NIST Cybersecurity Framework
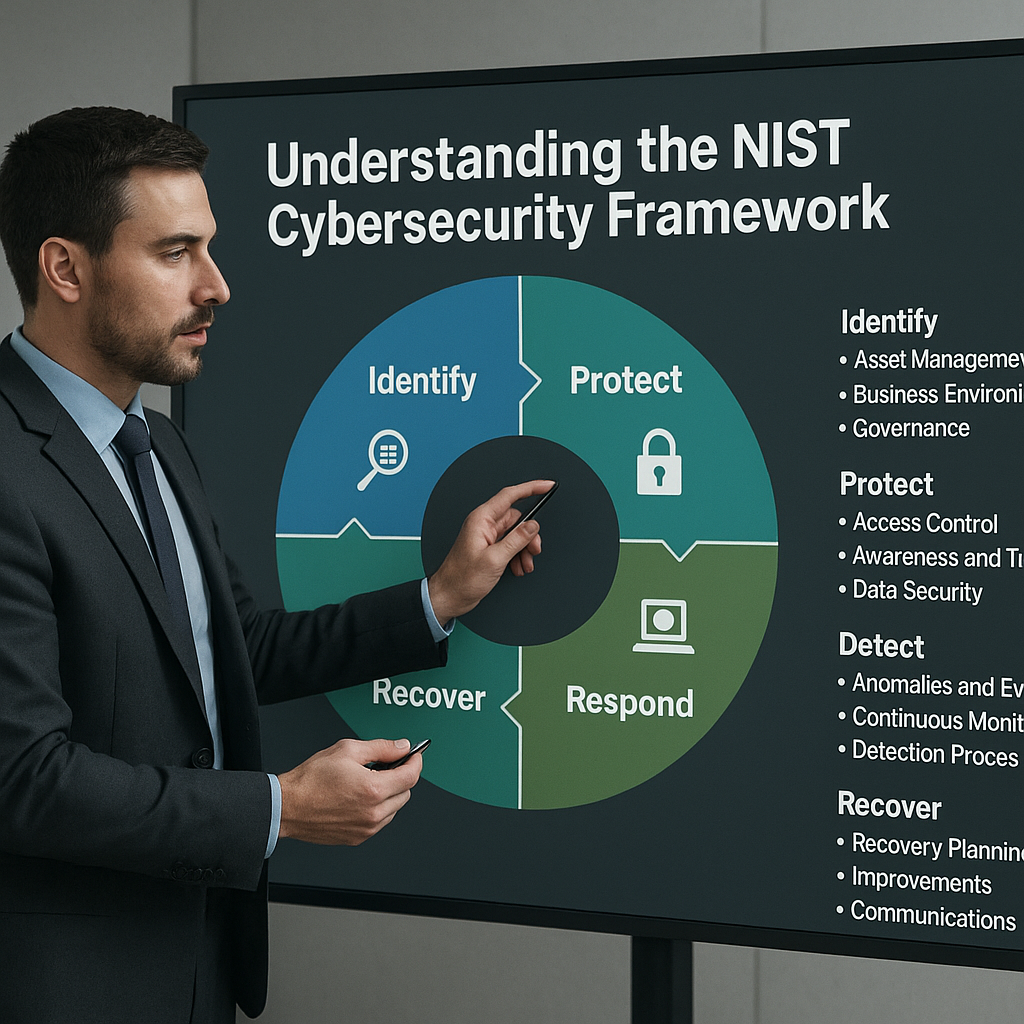
At the heart of the Framework lie five primary functions that provide a high-level, strategic view of the lifecycle of managing cybersecurity risks. Each function is crucial for developing a mature and cohesive security program.
Identify
- Inventory of assets, systems, data flows, and human resources
- Risk management processes and governance structures
- Establishment of organizational roles and responsibilities
Protect
- Access control policies to limit unauthorized entry
- Implementation of secure configurations and maintenance
- Employee training and awareness programs
- Data encryption and backup strategies
Detect
- Continuous monitoring through intrusion detection systems
- Security information and event management (SIEM) integration
- Regular vulnerability scans and threat intelligence
Respond
- Incident response planning and playbooks
- Communication protocols with stakeholders and external parties
- Forensic analysis and containment measures
Recover
- Disaster recovery and business continuity plans
- Post-incident review and lessons learned
- Processes for system restoration and validation
Implementing the CSF in a Business Context
Integrating the Framework into existing business processes requires careful planning, cross-functional collaboration, and a clear roadmap. The following steps outline how organization leaders can translate the CSF into actionable initiatives.
- Executive Sponsorship: Secure support from senior management to ensure adequate resources and alignment with corporate objectives.
- Define current maturity Profile by mapping existing controls to CSF categories and subcategories.
- Establish a target Profile that reflects desired security outcomes and risk appetite.
- Perform a gap analysis to identify areas needing improvement or additional investment.
- Develop a prioritized action plan with clear timelines, owners, and success metrics.
- Leverage cross-departmental teams—IT, legal, HR, finance—to foster a unified approach.
- Regularly update Profiles to reflect changes in the threat landscape or business strategy.
By treating cybersecurity as a shared responsibility, organizations can embed resilience into their operations, reduce silos, and accelerate decision-making when facing emerging threats.
Benefits and Challenges of Adopting the CSF
While the CSF delivers a wealth of advantages, it also presents challenges that require careful navigation to maximize value.
Key Benefits
- Standardization: Provides a common language for stakeholders to discuss risks and controls.
- Regulatory alignment: Simplifies compliance with laws such as GDPR, HIPAA, and SOX.
- Enhanced visibility: Encourages comprehensive asset tracking and threat monitoring.
- Business continuity: Reduces downtime through robust recovery planning.
- Competitive advantage: Demonstrates strong security posture to partners and customers.
- Continuous improvement: Promotes iterative refinement of security processes based on metrics.
Common Challenges
- Resource constraints: Budget and skilled personnel may be limited.
- Complexity: Aligning multiple frameworks and standards can lead to overlap.
- Resistance to change: Organizational culture may inhibit adoption of new practices.
- Integration hurdles: Legacy systems often lack native support for modern security controls.
- Measuring success: Defining appropriate metrics and key performance indicators (KPIs) can be difficult.
Addressing these challenges demands a phased approach, starting with high-impact, low-effort initiatives to build momentum and demonstrate quick wins.
Best Practices for a Sustainable Cybersecurity Posture
To ensure longevity and effectiveness, cybersecurity efforts must evolve alongside business growth and technological advancements. The following best practices can strengthen the Framework’s outcomes over time.
- Continuous Monitoring: Adopt automated tools and dashboards to track anomalies in real time.
- Security Awareness: Conduct regular training sessions and phishing exercises to reinforce employee vigilance.
- Third-Party Risk Management: Vet vendors through standardized questionnaires and performance assessments.
- Change Management: Integrate security considerations into project management lifecycles and DevOps pipelines.
- Incident Drills: Simulate cyber incidents quarterly to validate response plans and communication channels.
- Metrics and Reporting: Define and review KPIs such as mean time to detect (MTTD) and mean time to respond (MTTR).
- Governance Framework: Establish a cybersecurity steering committee to oversee policy updates and risk reviews.
- Supply Chain Security: Implement controls that extend security requirements to suppliers and service providers.
- Executive Dashboards: Provide leadership with clear, concise risk and compliance reports.
- Adaptive Planning: Reassess strategies after significant incidents or changes in business objectives.
Through these practices, organizations can maintain a dynamic defense posture that not only counters current threats but also anticipates future challenges. The NIST Cybersecurity Framework, when fully embraced and continuously refined, becomes not just a compliance checkbox but a driver of strategic resilience and business value.