
The Connection Between Physical and Cybersecurity
Organizations are increasingly recognizing that safeguarding assets extends beyond digital firewalls. A holistic approach demands seamless collaboration between physical measures…

Organizations are increasingly recognizing that safeguarding assets extends beyond digital firewalls. A holistic approach demands seamless collaboration between physical measures…

Building a resilient business demands more than just cutting-edge technology—it requires a workforce equipped to spot and respond to evolving…

Securing organizational assets has never been more critical as threat actors evolve their tactics daily. Businesses of all sizes must…

The Role of Encryption in Data Security explores how modern organizations protect sensitive information against evolving threats. Effective encryption strategies…

Protecting a company’s sensitive information is not merely an IT concern; it is a critical aspect of overall business security….
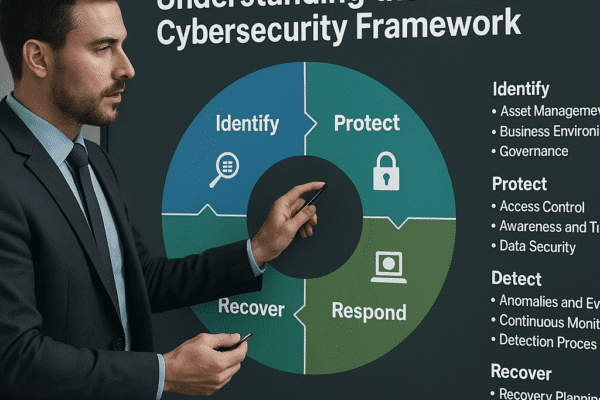
The NIST Cybersecurity Framework (CSF) has become a cornerstone for organizations seeking to strengthen their digital defenses while aligning security…

Effective communication channels are central to sustaining a competitive edge and maintaining stakeholder trust. Protecting sensitive data as it traverses…

Organizations facing a breach must act swiftly to limit damage, restore operations, and protect their reputation. This guide outlines practical…

Effective defenses against ever-evolving cyber adversaries demand proactive measures that extend beyond standard security protocols. Regular penetration testing offers organizations…

The financial sector faces an increasingly **complex** cyber environment where attackers exploit any weak link. Institutions must navigate a blend…